Ensure security at all phases, from development to production.
Integrating security into the CI/CD pipeline, often referred to as DevSecOps, ensures that security checks are automated and embedded throughout the software delivery lifecycle.
Vittal Angadi
5/8/20241 min read
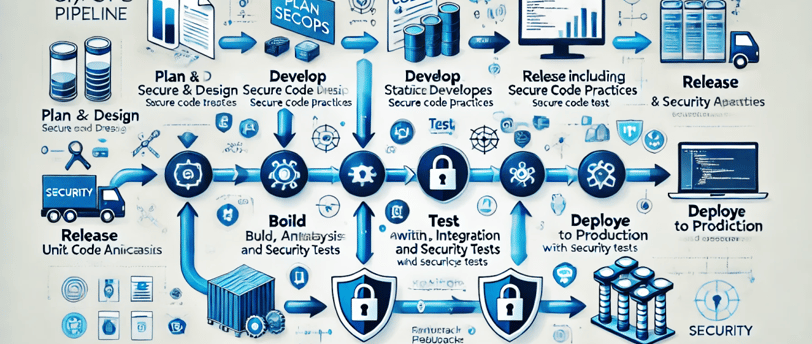
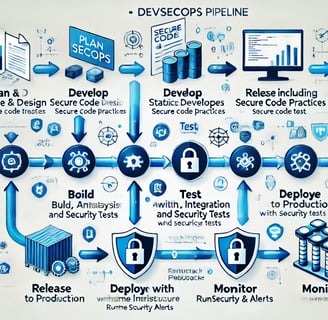
Integrating security into the CI/CD pipeline, often referred to as DevSecOps, ensures that security checks are automated and embedded throughout the software delivery lifecycle. Here's how you can approach it effectively:
1. Plan Security in the Pipeline
Threat Modeling: Analyze the application's architecture to identify potential threats early.
Define Security Policies: Clearly define security requirements and standards.
Compliance Checks: Map the pipeline to regulatory standards like GDPR, ISO 27001, or PCI DSS.
2. Source Code Security
Static Application Security Testing (SAST): Integrate tools like SonarQube, Checkmarx, or Fortify to scan code for vulnerabilities during the build phase.
Dependency Scanning: Use tools like OWASP Dependency-Check, Snyk, or WhiteSource to identify vulnerabilities in third-party libraries.
Secrets Management: Use tools like GitGuardian or Talisman to ensure sensitive data (e.g., keys, passwords) is not committed to repositories.
3. Secure Build Process
Use Trusted Build Environments: Use isolated and secure build servers.
Immutable Builds: Ensure builds are immutable and signed for verification.
Container Scanning: Tools like Aqua Security or Trivy can scan Docker images for vulnerabilities.
4. Automated Security Testing
Dynamic Application Security Testing (DAST): Test running applications for runtime vulnerabilities using tools like OWASP ZAP or Burp Suite.
Interactive Application Security Testing (IAST): Combine SAST and DAST in runtime environments (e.g., Contrast Security).
Penetration Testing Tools: Use automated tools like Metasploit or Nessus for periodic scans.
5. Secure Deployment
Infrastructure as Code (IaC) Scanning: Scan Terraform, CloudFormation, or ARM templates using tools like Checkov, Terrascan, or Bridgecrew.
Policy-as-Code: Implement tools like OPA (Open Policy Agent) to enforce compliance.
Secure Secrets Management: Use vaults like HashiCorp Vault or Azure Key Vault for secrets injection during deployment.
6. Runtime Security
Monitoring and Alerting: Implement tools like Prometheus, ELK Stack, or Datadog with security alerts.
Endpoint Security: Use tools like Falco or Sysdig for real-time security monitoring of workloads.
Web Application Firewall (WAF): Deploy WAFs to protect against common threats like SQL injection or cross-site scripting.
7. Continuous Feedback and Improvement
Post-Mortem Analysis: Conduct root cause analysis for security incidents.
Regular Updates: Continuously update tools and configurations to handle new vulnerabilities.
Security Training: Educate the team on secure coding practices and threat awareness.
